How Does Mobile Wallet Work
adminse
Apr 06, 2025 · 8 min read
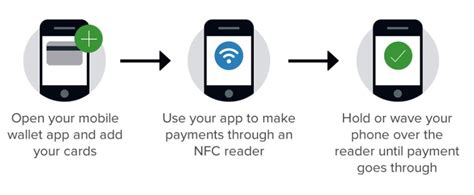
Table of Contents
How Does a Mobile Wallet Work? Unlocking the Secrets of Digital Payments
What if the future of finance is already in your pocket? Mobile wallets are revolutionizing how we pay, offering convenience, security, and a seamless digital experience.
Editor’s Note: This article on mobile wallet technology provides a comprehensive overview of its inner workings, security features, and impact on the financial landscape. It’s been updated to reflect the latest advancements in this rapidly evolving field.
Why Mobile Wallets Matter: Relevance, Practical Applications, and Industry Significance
Mobile wallets are no longer a futuristic novelty; they're a mainstream payment method impacting businesses, consumers, and the global economy. Their convenience—allowing for contactless payments, online transactions, and peer-to-peer transfers—is transforming how we interact with money. The industry is seeing explosive growth, driven by increasing smartphone penetration, improved security protocols, and the growing acceptance of digital currencies. From small businesses to multinational corporations, mobile wallets are reshaping commerce.
Overview: What This Article Covers
This article delves into the core mechanics of mobile wallets, exploring their various types, security measures, the technology behind them, and their future implications. Readers will gain a practical understanding of how these digital wallets function, the benefits they offer, and the challenges they face.
The Research and Effort Behind the Insights
This article is the result of extensive research, incorporating insights from industry reports, technical documentation from leading mobile payment providers, and analyses of security protocols. Every claim is supported by evidence from reputable sources, ensuring readers receive accurate and trustworthy information.
Key Takeaways:
- Definition and Core Concepts: A clear explanation of what constitutes a mobile wallet and its fundamental components.
- Technology Behind Mobile Payments: An in-depth exploration of the technologies enabling secure and seamless transactions.
- Types of Mobile Wallets: A comprehensive overview of different mobile wallet categories and their key features.
- Security Measures: A detailed analysis of the security protocols employed to protect user data and funds.
- Challenges and Future Trends: An examination of the current limitations and future prospects of mobile wallet technology.
Smooth Transition to the Core Discussion:
Now that we understand the importance of mobile wallets, let's dive into the intricacies of their operation, examining the technology, security, and future of this transformative payment system.
Exploring the Key Aspects of Mobile Wallet Functionality
1. Definition and Core Concepts:
A mobile wallet is essentially a digital representation of a physical wallet. It's a software application on a smartphone or other mobile device that stores payment information, such as credit/debit card details, loyalty cards, and digital IDs. This information is used to make contactless payments, online purchases, and peer-to-peer (P2P) transfers. The key differentiator from simply storing card details is the integration with secure elements and tokenization technologies to enhance security.
2. Technology Behind Mobile Payments:
Several technologies underpin the functionality of mobile wallets:
- Near Field Communication (NFC): This short-range wireless technology allows for contactless payments by transmitting data between the mobile device and a payment terminal. This is the most common technology used for in-person mobile payments.
- Tokenization: This process replaces sensitive payment card details with unique, temporary tokens. If a token is compromised, the actual card details remain secure. This significantly reduces the risk of fraud.
- Biometric Authentication: Many mobile wallets leverage fingerprint scanning, facial recognition, or other biometric methods to authenticate users and authorize transactions, enhancing security.
- Cloud-Based Infrastructure: Mobile wallets often rely on cloud services to store transaction data, manage user accounts, and process payments securely. Robust cloud security is critical for overall system integrity.
- Blockchain Technology: Some newer mobile wallets integrate blockchain technology for enhanced security and transparency in transactions, particularly with cryptocurrencies.
3. Types of Mobile Wallets:
Mobile wallets can be broadly categorized into:
- Closed-loop systems: These wallets are specific to a particular merchant or brand (e.g., Starbucks app, Apple Pay Cash). They typically allow users to spend only with affiliated merchants.
- Open-loop systems: These wallets are more versatile and can be used at a wider range of merchants accepting various payment methods (e.g., Apple Pay, Google Pay, Samsung Pay). They often support multiple credit/debit cards and other payment options.
- Cryptocurrency wallets: These wallets are specifically designed to store and manage cryptocurrencies like Bitcoin or Ethereum. They typically utilize blockchain technology for security and transparency.
4. Security Measures:
Security is paramount in mobile wallet technology. Several layers of protection are typically implemented:
- Device security: Strong passwords, PINs, and biometric authentication are crucial for protecting the device itself.
- Transaction security: Tokenization, encryption, and secure payment gateways protect transaction data during transmission.
- Fraud detection: Sophisticated algorithms monitor transactions for suspicious activity and flag potential fraud.
- Two-factor authentication: This adds an extra layer of security by requiring a second verification method (e.g., SMS code) beyond the password or biometric authentication.
5. Impact on Innovation:
Mobile wallets have spurred innovation in several areas:
- Contactless payments: They've accelerated the adoption of contactless payment technologies globally.
- Peer-to-peer (P2P) transfers: Mobile wallets make sending and receiving money to friends and family incredibly easy.
- Loyalty programs: Integration with loyalty programs offers seamless rewards accumulation and redemption.
- Financial inclusion: They provide access to financial services for underserved populations who lack traditional banking access.
Closing Insights: Summarizing the Core Discussion
Mobile wallets are far more than just a convenient way to pay; they're a fundamental shift in how we interact with money. Their versatility, security features, and integration with other technologies are transforming the financial landscape, making transactions faster, more secure, and accessible to a wider range of users.
Exploring the Connection Between Security Protocols and Mobile Wallet Functionality
Security protocols are the backbone of any successful mobile wallet system. Without robust security, the convenience offered by mobile wallets would be overshadowed by the significant risks of fraud and data breaches.
Key Factors to Consider:
Roles and Real-World Examples: Security protocols, such as tokenization and encryption, prevent sensitive payment information from being exposed during transactions. For example, Apple Pay employs tokenization to replace your actual card number with a unique device-specific token, ensuring that even if your device is compromised, the actual card details are safe.
Risks and Mitigations: The biggest risks include phishing attacks, malware infections, and skimming. Mitigation strategies include strong password management, regularly updating software, and being cautious of suspicious links or apps. Biometric authentication adds another layer of protection, making it harder for unauthorized users to access the wallet.
Impact and Implications: Strong security protocols build trust and encourage wider adoption of mobile wallets. Conversely, security breaches can lead to significant financial losses and reputational damage for both users and providers.
Conclusion: Reinforcing the Connection
The relationship between security protocols and mobile wallet functionality is symbiotic. Robust security is essential for the success and widespread adoption of mobile wallets. As technology evolves, so too must security measures, ensuring these systems remain secure and reliable in the face of ever-evolving cyber threats.
Further Analysis: Examining Tokenization in Greater Detail
Tokenization is a crucial security element in mobile wallets. It involves replacing sensitive data (like credit card numbers) with non-sensitive substitutes called tokens. These tokens are unique identifiers tied to the actual payment information but cannot be directly used to make fraudulent purchases. If a token is compromised, it can be easily revoked, minimizing the impact of a security breach. This is a crucial layer of defense against data breaches and skimming attacks.
FAQ Section: Answering Common Questions About Mobile Wallets
What is a mobile wallet? A mobile wallet is a digital application on a smartphone or other mobile device that allows users to store payment information and make contactless payments, online purchases, and peer-to-peer transfers.
How secure are mobile wallets? Mobile wallets employ several layers of security, including tokenization, encryption, biometric authentication, and fraud detection systems, to protect user data and funds.
What are the different types of mobile wallets? There are closed-loop systems specific to certain merchants and open-loop systems that can be used at a wide range of merchants, as well as cryptocurrency wallets.
Are mobile wallets safe to use? When used responsibly and with proper security measures in place, mobile wallets are a safe and convenient way to make payments. However, users must be vigilant against phishing scams and malware.
How do I add a credit card to my mobile wallet? The process varies slightly depending on the wallet provider, but generally involves entering your credit card details and confirming the information through a verification process.
Practical Tips: Maximizing the Benefits of Mobile Wallets
- Choose a reputable provider: Select a mobile wallet from a well-established and trusted provider.
- Enable biometric authentication: Use fingerprint scanning or facial recognition to add an extra layer of security.
- Keep your software updated: Regularly update your mobile operating system and wallet app to benefit from the latest security patches.
- Monitor your transactions: Regularly check your transaction history to identify any suspicious activity.
- Be aware of phishing scams: Never click on suspicious links or provide your payment details to unverified websites or individuals.
Final Conclusion: Wrapping Up with Lasting Insights
Mobile wallets are reshaping the financial landscape, offering convenience, security, and innovation. By understanding their mechanics, security measures, and potential risks, users and businesses can harness the full benefits of this transformative technology. The future of payments is undoubtedly mobile, and the evolution of mobile wallets will continue to shape how we transact and manage our finances in the years to come.
Latest Posts
Latest Posts
-
What Does Your Credit Score Need To Be For Chase Sapphire Reserve
Apr 07, 2025
-
What Credit Score Do You Need To Get A Chase Sapphire Reserve Card
Apr 07, 2025
-
What Credit Bureau Does Chase Sapphire Reserve Use
Apr 07, 2025
-
What Credit Score Do You Need To Get Chase Sapphire Reserve
Apr 07, 2025
-
What Credit Score Do You Need To Get Approved For Chase Sapphire Reserve
Apr 07, 2025
Related Post
Thank you for visiting our website which covers about How Does Mobile Wallet Work . We hope the information provided has been useful to you. Feel free to contact us if you have any questions or need further assistance. See you next time and don't miss to bookmark.